India’s digital landscape is booming. From e-governance initiatives like Digilocker (a platform for storing digital documents) and UMANG (a unified mobile app for accessing government services) to the proliferation of fintech, secure identity and access management (IAM) is paramount.
With a vision to create a robust, future-proof IAM framework, the Indian government is charting a course that transcends traditional boundaries and embraces the cutting-edge innovations of the digital age. This strategic roadmap not only aims to enhance citizen experiences but also fortifies the nation’s cybersecurity defenses, fostering an environment of trust and resilience in the digital realm.
Aadhaar, the world’s largest biometric ID system with over 1.3 billion enrollments, has laid a strong foundation for digital identity in India. It has significantly streamlined access to government benefits and subsidies, reducing leakages in welfare programs by an estimated 5% according to a 2016 World Bank study.
Aadhaar simplifies applying for subsidies and filing taxes, while Direct Benefit Transfer (DBT) ensures subsidies and payments reach beneficiaries directly. The 2017 Aadhaar Usage Report by UIDAI highlights that over Rs. 1.7 lakh crore ($24 billion) worth of subsidies were transferred via DBT using Aadhaar, enhancing the efficiency and transparency of the system.
However, challenges like privacy concerns and scalability necessitate a more holistic approach. India’s digital revolution hinges on secure and efficient Identity and Access Management (IAM). This future-proof system will address privacy concerns, ensure scalability, and empower users with greater control.
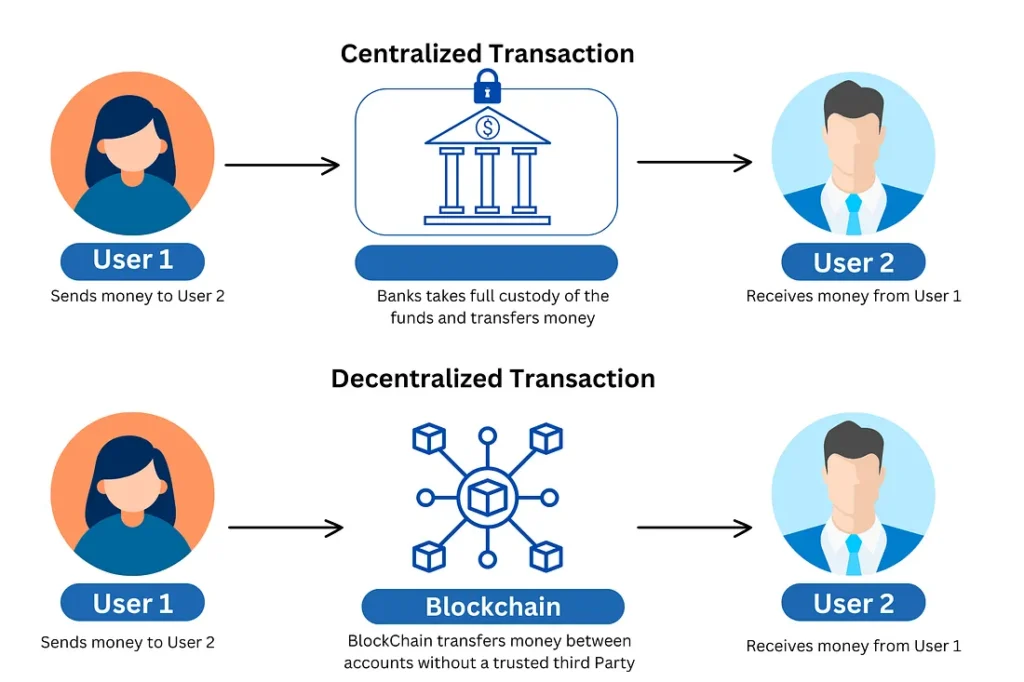
While Aadhaar has been a game-changer, the Indian government recognizes the potential of decentralized identity management systems. Here’s a glimpse into some ongoing initiatives and policy discussions:
2. Multi-factor Authentication (MFA)
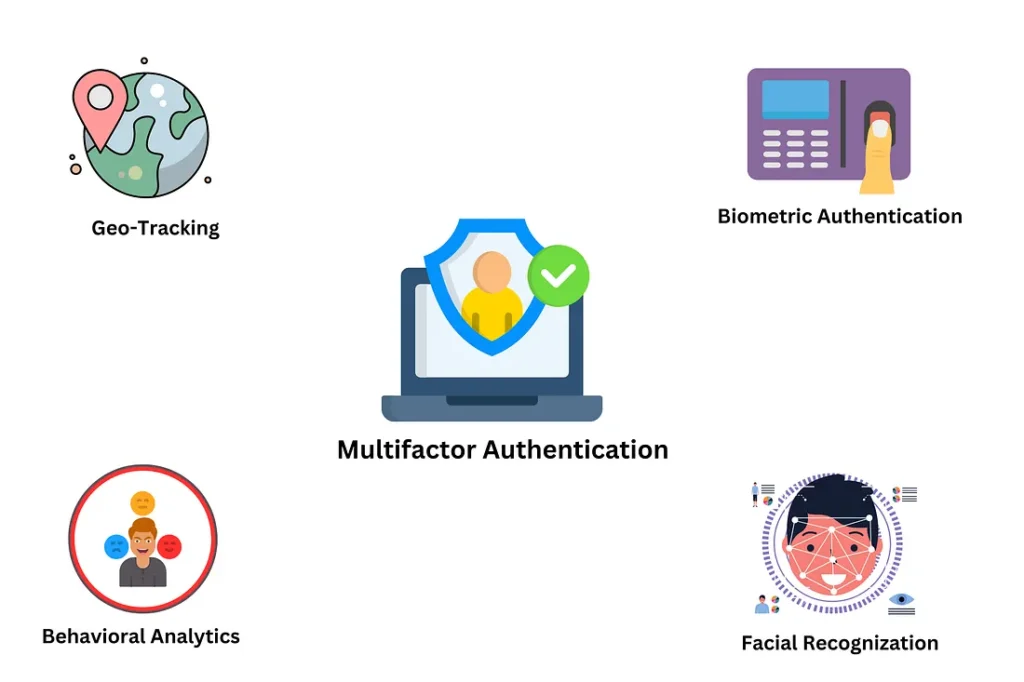
Statements from government bodies like MeitY have emphasized the need for a layered security approach which suggests exploring MFA features below.
3. Privacy-First Design: India Prioritizes User Control


As India forges ahead with its visionary IAM roadmap, ZTrust stands as a trusted partner, offering cutting-edge solutions and unwavering expertise to support this transformative journey. With a deep understanding of the Indian market, ZTrust provides a comprehensive suite of IAM solutions tailored to meet the nation’s evolving needs.
ZTrust’s robust IAM system powered by Zero Trust goes beyond just security. It enhances user experience by providing secure, single-login access to all applications, ensures compliance with data privacy regulations like GDPR, and supports innovation in emerging technologies like blockchain and AI, enabling security and protection from cyber threats.
As India embarks on its transformative IAM journey, success hinges on collaborative efforts from government agencies, private sector entities, and the broader technology ecosystem. Public-private partnerships, aligning with global IAM initiatives will facilitate cross-border interoperability. enabling seamless collaboration on digital projects and positioning India as a leader in identity and access management.
By fostering a collaborative ecosystem, India can leverage diverse expertise and resources to overcome challenges, address emerging threats, and seize new opportunities, ensuring an agile, adaptive, and resilient IAM framework.
Single Sign-On (SSO) offers a range of benefits for streamlining access management and enhancing security
Keeping track of many identities and passwords for different programs may be a challenging endeavor.
In today’s complex digital landscape, organizations face the daunting task of securing their critical assets